Smart Cities | IoT Security in a Hyperconnected Landscape

In the past decade, we have seen an explosion of non-traditional devices connecting to the internet, but with all the benefits of smarter and more responsive devices. The sheer size of the ever-expanding Internet of Things (IoT) poses an unprecedented security challenge for businesses and consumers alike.

The app associated with Osram Lightify's smart lightbulbs could potentially open a user's entire wifi network to outside attackers.
Image: Hacker News
Even small oversights in IoT security protocols can have far-reaching effects. Relatively simple security oversights led to some mocking press coverage recently on topics like hacked lightbulbs but the real situation can be far more grave. A bug found late last year on Apple’s HomeKit reportedly would allow hackers to unlock a home’s smart door, and recently the FDA was forced to recall almost 450,000 pacemakers already implanted in patients because their poor security protocols left them open to attacks that could rapidly deplete battery life or potentially impact a patient’s heartbeat.

In 2016, the FDA was forced to recall over 450,000 connected pacemakers thought to be vulnerable to potentially life-threatening hacks. Image: The Guardian.
Even the lightbulb case was a much bigger deal than the jokes implied. The ‘Things’ in the IoT are only one aspect of a larger more connected network. So, a breach at one point could theoretically lead to a takeover of an entire architecture. Osram Lightify light bulbs require WiFi to connect to a network and a companion app for use and monitoring. As it turned out, that companion app was storing unencrypted copies of WiFi passwords; in a worst-case scenario, a breach on anyone connected bulb could lead to an attacker gaining access to private information contained on all devices connected to that same network. Speaking to Digital Trends, University College London Cybersecurity expert Dr. Angela Sasse said:
This is not just about being able to manipulate the lightbulbs The vulnerabilities here could give somebody access to control the network itself and that’s a very serious issue. In this day and age, you would regard that as an unacceptable security flaw. It’s a well known thing that you don’t store passwords like that — it’s really elementary.
Main IoT Security Threats aren’t New
So, as the IoT continues to rapidly scale, so do potential entry points for malicious actors. With all of the reports about security threats related to IoT, business leaders can be forgiven for being anxious. But, having an understanding of basic security/privacy measures and adopting them early can dramatically reduce potential roadblocks in adopting IoT solutions.
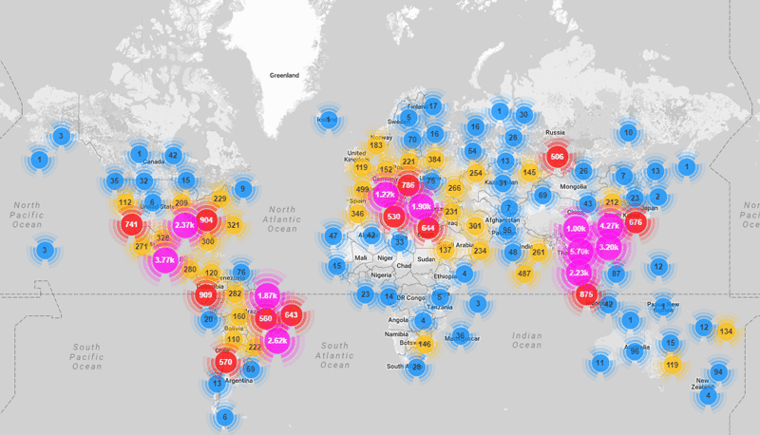
In 2016, Heatmap showed the scope and scale of Mirai's effects. Source: The Security Ledger
One of the most widely-reported IoT-related attacks came in 2016 when a botnet called Mirai ran a distributed denial of service (DDoS) attack that disrupted many of the world’s most popular websites (such as PayPal, Twitter, and Spotify). While the magnitude of this attack was alarming, an analysis by security giant Symantec found that the botnet worked in a relatively simple way: it simply blitzed devices with a list of well-known default usernames and passwords. Simply configuring the devices exploited by Mirai to not accept default credentials (some as simple as username: ‘user’, password: ‘1234’) could have dramatically mitigated the attack.
Key Points in the Attack on Connected ‘Things?’
Broadly speaking, the things/devices themselves joining the IoT have a number of potential vulnerabilities. Good early planning within a solid SDLC (Security Development Life Cycle) by the device manufacturer will make the devices themselves as secure as possible. A 2015 ISACA report highlighted a number of common vulnerabilities in poorly-designed IoT devices, as well as the security solutions best able to mitigate any potential issues:
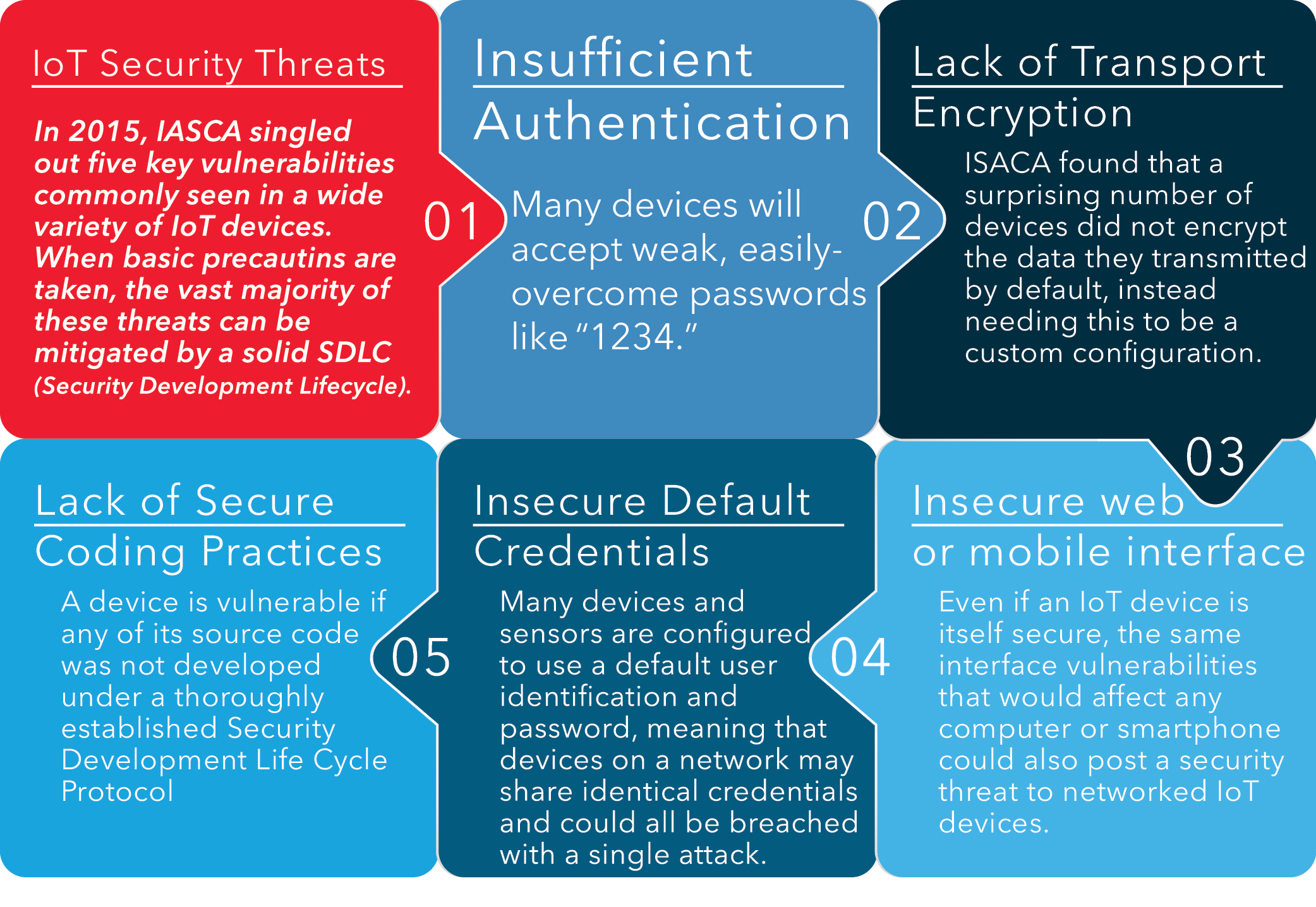
Developers working on IoT devices should be well aware of these potential vulnerabilities, and most would ensure that none of the above issues actually made it through development to an end-user. Still, with billions of devices as part of the broader IoT network, business professionals and regular consumers alike should know the basics and be able to speak competently with vendors about them before making a sizable investment in any IoT solution.
In addition to the devices themselves, business leaders need to be sure their existing security architecture is well-developed and ready to absorb all of the new devices coming onto the network. Beyond special considerations for the devices themselves, protecting a hyperconnected network actually looks quite a bit like protecting a traditional network. Secure Sockets Layer (SSL) transport layer security, server monitoring, and well-thought-out database access controls will cover the vast majority of attack scenarios at all levels of the IoT architecture.
Even with a wider surface area for attackers to exploit, the benefits of IoT still vastly outweigh security concerns. Most of the vulnerabilities on connected devices are relatively simple, and early introduction of security into the overall adoption cycle and some good old common sense should protect a hyperconnected network against the vast majority of potential IoT-specific threats.


